Foundational Research to Identify Business Opportunities.
At Cisco, I informed 3-5 years of business roadmap by leading a deep dive foundational research study.
Impact includes identifying four areas for further research, informing survey instruments, and defining market study parameters.
*Under NDA - Rich on story, limited on data*
Role
Design Strategy & Research Intern
Organization
Cisco Secure
Duration
8 Weeks
Key Activities
Discussion guide
Participant recruitment
Interviews - moderation to synthesis
Insight socialization
Actionable recommendations
Tools
Dovetail, Miro, Figma
Collaborators
Design Researchers & Strategists
Business Innovation Teams
Data Analytics Team
Design Ops
Here is my story!
What was the study?
This strategy research project was done with the business strategy and innovation team.
The project's ultimate goal was to identify business 3-5 years business development opportunities for Cisco Secure.
What had been done already?
Before I joined, Cisco had already conducted a study and identified 4 key unmet customer needs. Those being..
01 Business Value Security
03 Fragmented CloudTransition
02 Data Compliance & Regulation
04 Decentralized Data & Distributed Access
What did I choose to do?
In the ongoing phase of the study, I chose to conduct a deep dive into the 4 unmet customer needs to identify the exact opportunities for business development.
Interviews
12 Semi Structured Interviews
60 minutes each
Over phone call
But it took me time to understand the study because..
So to understand the study and the domain..
I seeked mentorship from my manger.
I had 1:1 with diverse teams within Cisco to develop my own perspective.
And it helped me prepare the interview guide & Project timeline.
Let me give you an example of Decentralized Data & Distributed Access.
1st draft By myself
With people and data being in multiple places, how do you identify that the appropriate person is accessing the data they are entitled to?
2nd draft With manager
What are some security complexities due to the introduction of hybrid working?
What are some of the challenges of having data stores in multiple places?
What are some challenges in having multiple data storage platforms?
3rd draft With cross-functional teams
What are some of the security measures which are implemented at the data end? ( Imagine a line. On the left, you have the user; the line indicates the access, and on the right is the data)
However, recruiting participants was a different ballgame.
At first, I was targeting specific roles for each study topic. But, soon, I realize that roles & titles keep changing across companies.
Therefore, I focused on job responsibilities and shared them with the recruiting agency & they got back with the appropriate candidate.
Decentralized Data & Distributed Access
Security professionals who define and managers access to data and identity across multiple systems (cloud-native applications)
IT Professionals who work closely with the security team to ensure the infrastructure is configured as per the org’s data security and access needs.
People responsible for demonstrating the maturity of their data security to potential clients so that it drives business.
Paraphrasing of responses by participants.
And the reason I failed were
Sticking too tightly to the interview guide.
I knew I could have done better because
Soon came the first interview & I could have done better
Change in tone of the participant
Trying to cover too many touch points.
I changed my interviewing technique.
I started following the thread by identifying participants’ excitement towards specific questions.
I leaned my interviewing scale towards unstructured interviews.
But then, I adapted.
When I could not understand, I told the subject matter expert that I was new to the field.
“I am curious to know what the study is about'!”
Participant 7
“This is an interesting question.”
Participant 5
And the following interviews were a breeze.
“It has been fun talking to you!”
Participant 8
I presented my findings to different stakeholders after each topic on a weekly cadence.
The teams were curious to know what I learned, and so was I to share.
But discovering nuanced insights was totally different.
Interview A
Interview B
Interview C
I followed a thread in each of the interviews. And by following a thread, the data I got from each interview felt disjointed. Therefore, I was unable to discover insights.
To learn how to find themes & discover insights
I had conversation with senior managers to overcome my bias.
I connected with other researchers to see how they discover insights & priorities their finding.
Step
Analyzed each interview in dovetail and noted the important data points and their context.
And it helped me develop a novel 3 step process to discover insights using thematic & narrative analysis.
Step
Brought all the data points with contex from each interview into a shared Miro board.
Step
Looked at all the data points together to understand how specific points realte with each other to identify the underlying insights.
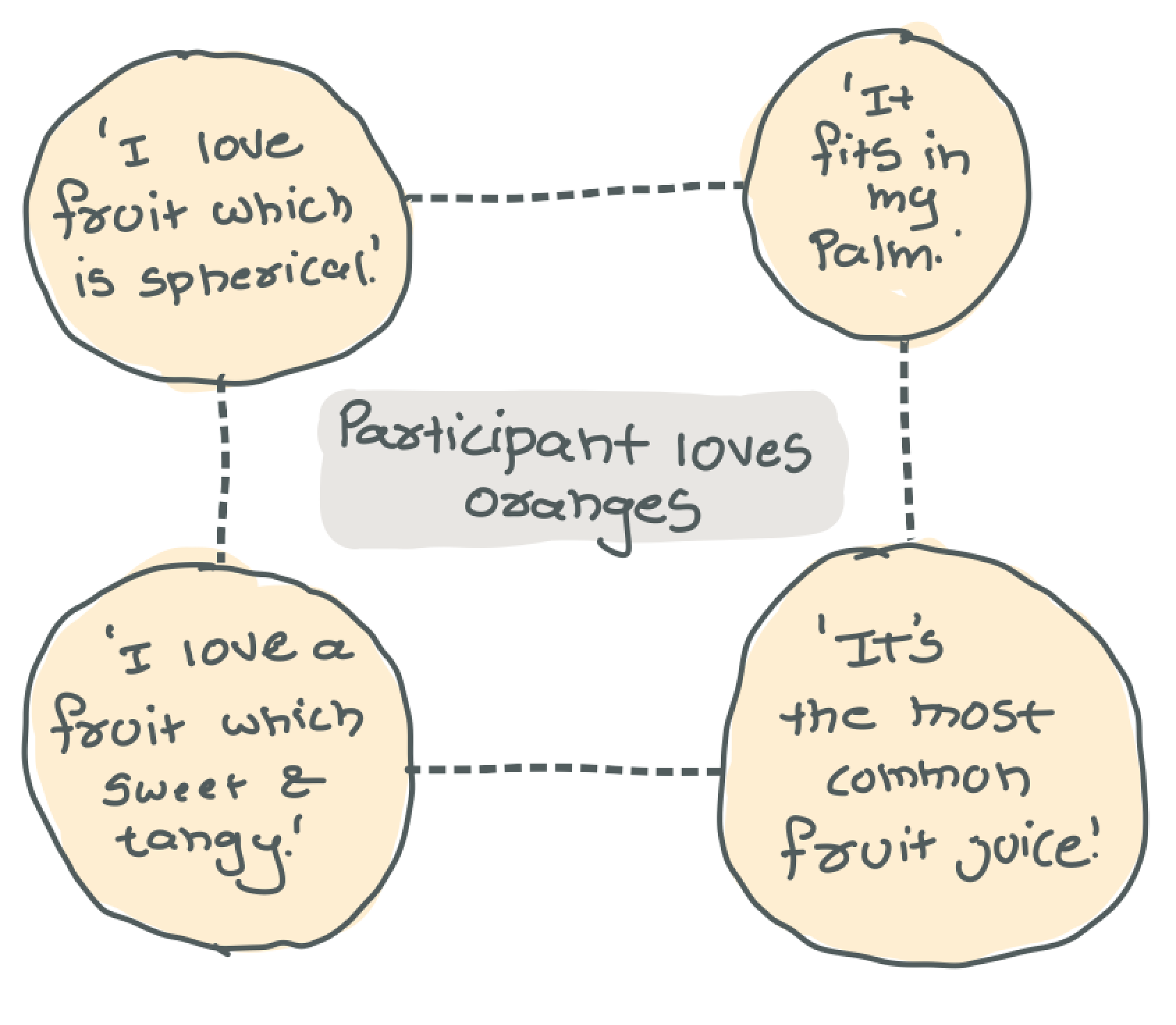
This is how the process looks.
Insight - All participants love oranges. However, each participant describes it differently.
Doing this over and over, I was able to..
I created diagrams to explain the complex insights.
But the insights were hard to explain. Therefore...
Which I then presented to various stakeholders.
Recommendation - Cisco should look into data immutability.
Inform market research
Create a survey to understand the market sentiment
And the stakeholders used the data to..
Short term impact
Identify areas for further research in the unmet needs.
Long term Impact
The research I did will help Cisco Secure decide what technology to buy, invest or build in the next 3-5 years.
Ultimately,
My Impact @ Cisco
The Design Thinking team reached out to me to ask how I discovered insights so quickly and if I could share my technique with other teams.
My biggest takeaway is..
Each thing you do has its own set of drawbacks. But, the next thing you do should address those drawbacks.